UPDATE: August, 2014: Apparently security researchers now have access to the master database of keys. IF you have been infected with this virus and still have any of the files, you MAY be able to get the unlock code for free at: https://www.decryptcryptolocker.com/
Have you ever heard of someone getting a phone call from say “Microsoft”, “Rogers”, “Bell”, “RCMP”, “FBI”, “Tech Support” and then heard how they lost all of their data and had to pay?
Ever had one of these calls yourself?
Since I moved to the Moncton area in the summer of 2013, I have had 3 such calls to my residence.
What the companies are trying to push, is something called a CryptoLocker virus. Basically the scam is as follows: A telemarketer, calls you with either a blocked private, or fake number. They explain they are calling from one of the many companies above and explain that your computer is infected and you are at all sorts of risks and need help immediately, and typically they say its completely free!
What they then do is they walk you through a few things: 1) They disable your anti virus, sometimes explaining its faulty and you need a new one and 2) They install their “virus”. That program “scans” your computer and looks rather convincing.. Right up until it finishes, and at that point they either hang up, or start the next phase of the scam..
Ransom
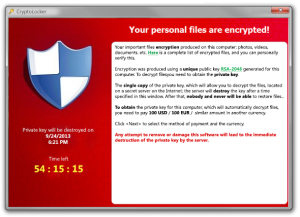
What happened was that while your computer was being “Scanned” the software was using heavy grade (RSA 2048 Bit) encryption to target your files. It typically goes after your most “valuable” files possible. It will go after your personal documents and recent files first, then continue to move through your system.
What is far worse, for business, is that it will start going after network and attached drives. Once its done you will see something similar to this:
Once the process has started you get 72 hours to either Pay, or lose the data. This is where it can really get tricky.. The price you pay may just be the starting point. Once the people have infected you and they know you have valuable data, they can start squeezing you for money. The price is normally in a crypto currency, ever heard of Bitcoin? Well one of the suspected reasons its going up in value is because of this type of scam. Forbes magazine recently posted an article on the problem here. Some companies and individuals are reporting ransoms are now in the $3000 to $5000 USD per demand, and there is little guarantee that paying will get you your data back.
The money, is believed to go overseas to criminal elements in the former Russian republics.
How do you prevent it from happening?
First and foremost, its education. Its critical that you are not running programs that you aren’t expecting. If you download an excel file, or a PDF, and something suddenly starts running, stop it (New versions of windows have a basic protection that pops up and asks you if you are sure)
Secondly: Have a proper antivirus. Most newer anti virus programs can detect and handle this type of a virus, unless they are a) out of date or b) disabled by you or someone else (see below). Remember that the whole relationship between virus makers and anti-virus makers is very much the old analogy of better mousetrap, smarter mouse. Virus writers evolve and make their viruses faster, and disguise them better. Anti Virus makers have to play catch up. So even with the best anti-virus, education is still key.
Thirdly: Hang up on telemarketers that pull this scam. If you are so inclined report them to the RCMP or the FBI depending where you live. If the FBI or the RCMP really wants to talk to you, they have better ways to get in contact with you. If you are ever unsure if a person is really from Microsoft etc, ask them for a phone number to reach them, and Google it first!
What happens if I got infected, now what?
As discussed the first option, is the worst. Pay the ransom. Its the worst idea for two reasons 1) you have no idea how your information from the payment will be used 2) Paying people that do this only makes them continue to do it and 3) You have no guarantee that you will actually get your files back
The best option, recover from your backup. If you don’t have a backup, this is one of those life lessons that is going to hurt, badly. The type of encryption they use can “theoretically” be decoded, but it would take years and years and cost a fortune. That’s even if the “Theory” comes to play.
What can you do for me?
If you have already been hit with the virus, and you have no backup, then we can only help you get your systems back to running order again so you can start over.
If you have a backup, we can help you restore your backup and get you back and running as quick as possible.
If you are interested in protecting your computers from an attack like this, give use a call, or send in an email. We would be more than happy to explain how we can manage your IT needs, and educate your staff to minimize the risk for you and your company!
If you need help, just call “That Guy”
Trevor “That Guy” Vicars
Further Information:
The RCMP Anti Fraud Center http://www.antifraudcentre-centreantifraude.ca/english/Bulletin%202013-15_Crypto.html
The Internet Crime Complaint Center: http://www.ic3.gov/media/2013/131028.aspx
Wikipedia: http://en.wikipedia.org/wiki/CryptoLocker
Like and Follow us!